In the wee hours of December 1, 2016, Javed Khatri, a 22-year-old programmer (note: not a hacker) discovered a common security vulnerability/bug in the Narendra Modi app. Khatri was able to access the personal information of every registered user of the application through this vulnerability.
In the wee hours of December 1, 2016, Javed Khatri, a 22-year-old programmer (note: not a hacker) discovered a common security vulnerability/bug in the Narendra Modi app. Khatri was able to access the personal information of every registered user of the application through this vulnerability.
After sending out a tweet (below) to Modi to report the vulnerability, he approached a popular startup media organisation called YourStory to get the news out. YourStory published the vulnerability as an interview with Javed on December 2. However, the post was brought down by the media house when they realised it is still an ‘open bug’ (recognised by its builders and being worked upon) and issued a clarification later in the night. Firstpost also similarly reported it and took the story down. It was later picked up by other news organisations as well.In light of these events, I took a look at the Narendra Modi app and tried to replicate the bug. It took me less than five minutes to figure out the issue. Any mobile application communicates with a background server to store and retrieve information to be shown to the app’s user. This communication at the network layer of the application needs to be ideally encrypted to stop others from intercepting and listening on what the application is sending or receiving.
In the case of the current application, it was not encrypted, making it possible for Khatri to replicate application requests to the server and retrieve additional data. This type of attack is commonly known as a “man in the middle attack”. Julius Caesar was the first known person in history to devise a cipher to communicate with his generals securely even if the messenger (the ‘man in the middle’) was a spy or got intercepted.
The Narendra Modi app was designed to be another social media platform for Modi’s followers to engage and work for various political and social causes. Since it is designed as a social media platform, there are options in the application to search for someone, follow her, comment on her work and so on. All of these functions require a couple of application programming interfaces (APIs) that respond to the application with necessary details.
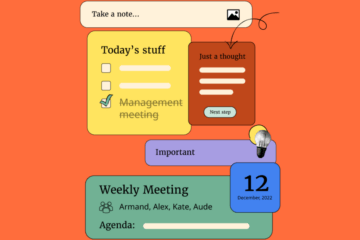
These APIs’ responses contain the personal information of the app’s users – including phone numbers, email addresses as well as the location and constituency of the application user. Crucially, it lets anyone request these details. When I requested these APIs by the end of the day on December 2, the app’s IT team had by then fixed some aspects of it – for one, by replacing contact numbers with “0000000000” and email id with “[email protected]” as a quick fix (a.k.a. a jugaad, a make-do).
But one can still look at the activities of a user through her last-seen time value, apart from her activity on the app exposing an active user to other political adversaries. This is a typical case of an information design flaw combined with lack of encryption and knowledge of information security. For a more formidable adversary, such as Chinese hackers or the NSA, all of this unencrypted data in the servers is easy to access.

The response as received later in the day through the APIs. Credit: iotakodali/GitHub
The issues around data being collected through the application for the BJP were highlighted recently by Aditya Kshirsagar, a tech writer, and have received wide coverage in the media. When it comes to the legal debate, on whether the application not having any security requires attention from government officials – it certainly does. Section 43A of the Information Technology Act mandates corporate bodies to compensate individuals affected by any breach of data. In this case, it is unknown to what extent criminals and other state players have exploited the vulnerability. As there are no mandatory disclosure laws in place in India, the BJP is not bound to disclose the extent of it. But any affected party can certainly sue them for compensation.
The security vulnerability in question is often found in most mobile applications, If you intercept your communications from your phone through a proxy, you will be able to discover to whom your GPS location is being shared every 30 seconds, or if your phone is downloading any content without your knowledge. Most new apps in India do not look into using encryption from the very start as the man-hours needed to be invested are high while skill-sets required to understand these issues are also wanting.
This brings up the debate on the use of encryption, which the Indian government has been discouraging by asking for digital certificate keys to every major communications application in the country. Further, the draft encryption policy released was draconian and comparable to that of countries with little or no human rights. Most government applications, whether Centre or state, are vulnerable to similar attacks and there is little interest in fixing them by the officials.
Knowingly or unknowingly, Khatri and media houses have brought the debate back around information security, which usually languishes backstage. And now that the Pandora’s box is open, one needn’t wonder what all vulnerabilities others are going to disclose. By the end of the day, Khatri had made statements that the vulnerability had been fixed and that he doesn’t want any media organisation using his work anymore. While it is his personal choice, the bigger question is whether the security is actually in place at all.
Significantly, this is not the first such security incident regarding the Modi government’s apps. In October 2015, another computer science engineer, Bhavyanshu Parasher, had reported the same security flaw in the API design of the official PMO application to the BJP IT team. It was fixed as the developer team saw fit and no disclosures were made. And this story was not accorded the same level of media coverage as was Khatri’s disclosure.
Khatri and media organisations like YourStory failed to responsibly disclose the vulnerability, instead went on reporting an active bug with much drama. How hard is it to report a vulnerability without calling it a hack or calling young programmers ‘hackers’? Khatri himself has made it clear it wasn’t a hack but a vulnerability disclosure. If the media wants to responsibly report on issues of cybersecurity and information security, perhaps they ought to begin by looking at their own applications first.
It needs to be noted that similar issues in government applications exist at large and receive little or no coverage. When you put college kids in a chair for a hackathon to solve India’s problems, what is it that the government, industry bodies are expecting? Most applications in the name of ‘Smart Cities’ and ‘Digital India’ are being made by students with no background in security and are being pushed onto government officials by unskilled businessmen dressed up as venture capitalists. There is little doubt about where the government-tech industry is going in terms of security: just down.
[Source:-Wire]